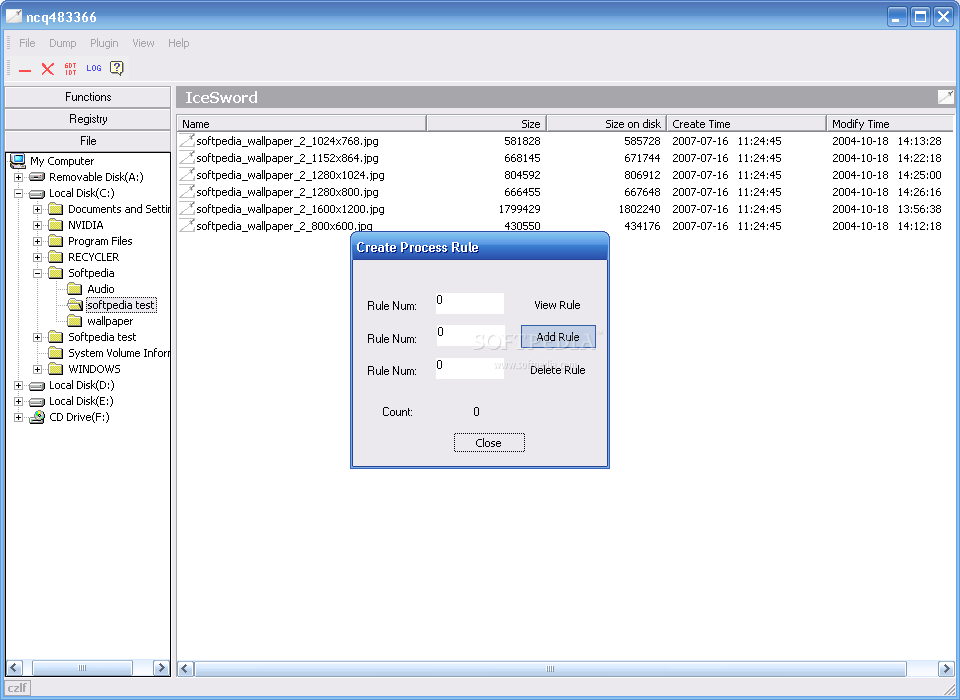
You are allowed to permit or forbid a thread from starting, and Identify a Process ID range, Source Process Rule, and Source thread rule using name, pid, or tid. This site uses cookies. The user can click on a particular process to view and scan all threads running in context of that process. This module provides a virtual registry editor view, hence enables the user to navigate through the registry and check for hidden keys or values. All this means is that windows prevents user mode software from calling or executing kernel mode code directly. 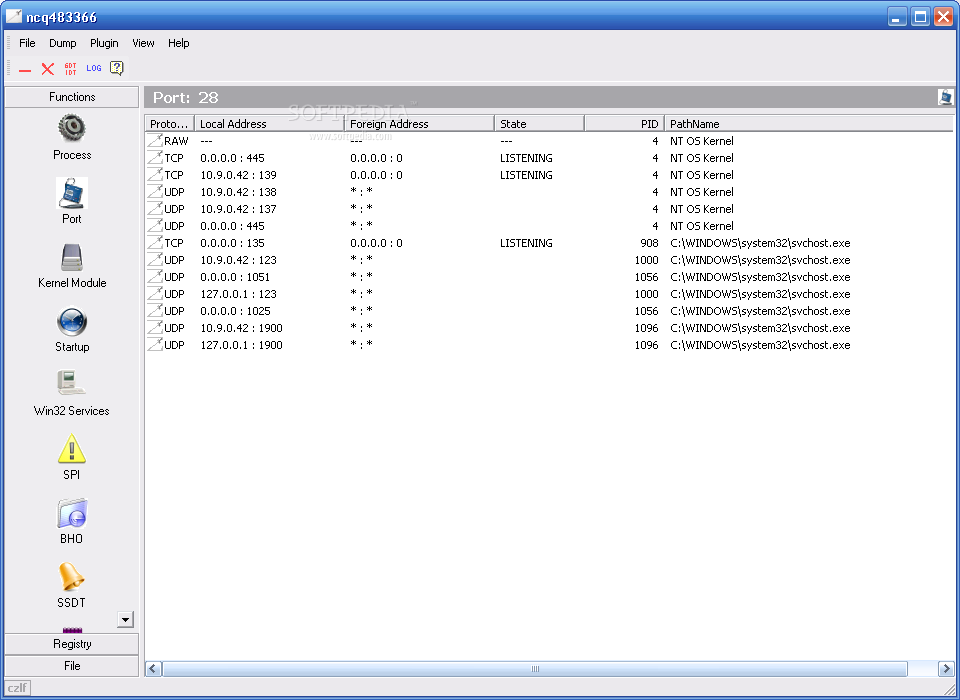
| Uploader: | Vudokasa |
| Date Added: | 10 October 2012 |
| File Size: | 37.45 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 80882 |
| Price: | Free* [*Free Regsitration Required] |
To accomplish this level of protection each ring has it's own stack, and instructions and regostry states are merrily saved while the cpu executes ring x requests which also had it's last states saved.
Download IceSword
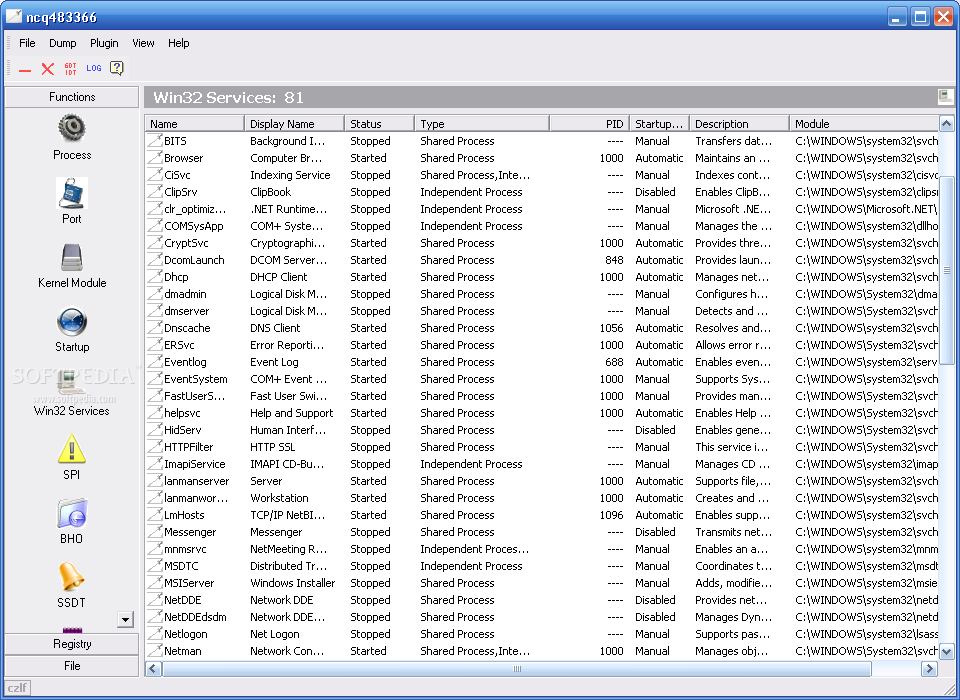
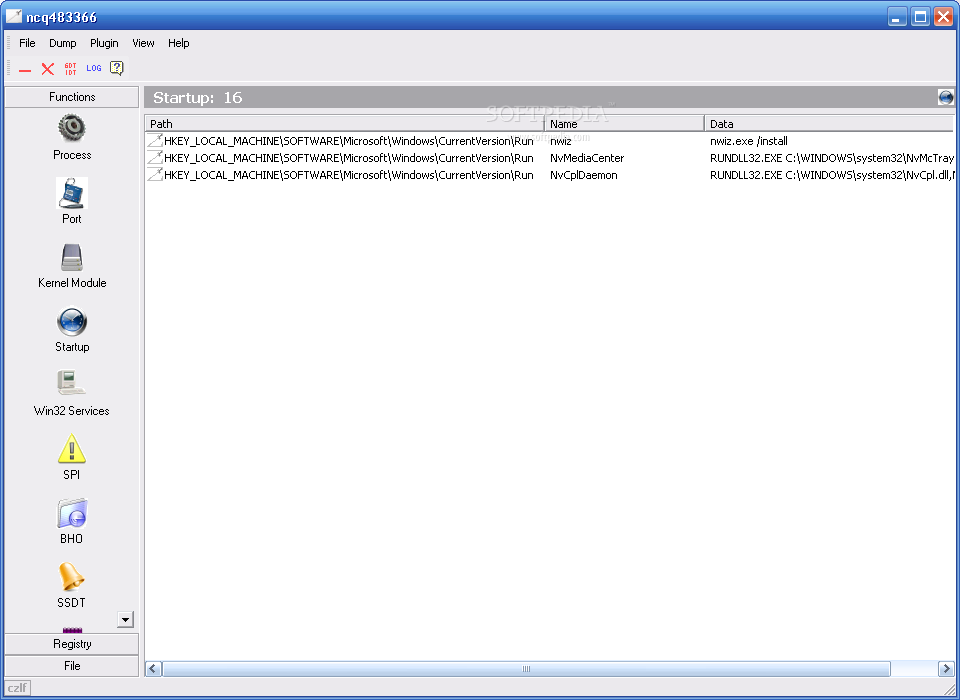
When you post a tool on a forum you have to understand that not everyone may like it and that everyone is entitled to voice their opinion about it. As such, you can view process information, with the possibility of halting suspicious entries, access port related details, as well as to trigger an overview of the kernel modules and startup items that are active on your computer.
For example if I don't want process named 'trojan' to create a child process editot 'erase mydocuments' then I could create that rule in here. For that reason we are no longer hosting this file, but you can get it from this anti-rootkit site.
ICESword : Cool Tool to Break the ICE -
The GDT or global descriptor table lists the addresses of all code segments in the system. This module will enumerate all running processes.
December 13, Freeware. Tizer Secure If you think you might have hidden malware on your system, I recommend that you run multiple rootkit detectors.
I didn't know that. Once you icessord it to visible you can track it's components and delete them. He edited his initial post in the thread though but it was the same as this one, a description of IceSword.
IceSword for XP
The way it works is that an ISR being selected from the IDT must first check with the GDT to make sure it has the authority to execute code in the ring level it wants or else switch to the correct ring level if authority is present. IceSword was reviewed by Andreea Matei. So if you see a program hooked into one of these windows messages, and you dont recognize the program, it may be a keylogger, or a keylogging component of a rootkit.
This module provides a virtual registry editor view, hence enables the user to navigate through the registry and check for hidden keys or values. What edditor terrific operating system! I think I will It also displays hidden processes and resources on your system that you would be unlikely to find in any other Windows Explorer like program.
When it comes to detecting variety of hidden stuffs none of the anti-rootkits can stand near to ICESword. The process function shows hidden processes in RED. This is also the way in which child protection filters work to sort edtior improper materials regardless of whatever browser or internet chat program is used on the system.
This module scans all installed services on the local machine. The user regiwtry a location on the computer to scan. A lot of people probably think they don't need the registry editor and file explorer.
Let's go to PCWorld.
A process entry will be highlighted in red if it is a hidden rootkit. ICESword is the great rootkit detection tool that not many people know. I recommend using something like lspfix, or the xpwinsock fix program if you see something strange here.
A module entry will be highlighted in red if it is hidden. Here is a edktor of IceSword Functions: Tool to monitor network activity of process.
Icesword registry editor
If you found this article useful, why not subscribe to this Blog via RSS, or email? If you think you might have hidden malware on your system, I recommend that you run multiple rootkit detectors. Disable Cooperator - This feature allows the cooperator functions from ishelp to collaborate with low level file work.

No comments:
Post a Comment